What's going on here, how do I use this?
The idea behind Punkspider is very simple - we're doing a bunch of complicated stuff to find insecurities in massive amounts of websites, with the goal of scanning the entire Internet. This extension just provides a simple way for you to find out if we've found vulnerabilities in a website that you use or own. There's just a few things that you need to know to get started if you are new to web security.
Why should I care?
Vulnerabilities in websites can be devastating to you as a user. If a website is storing your sensitive information, a single vulnerability could potentially cause this information to be stolen. For sites that aren't storing your information, they can be riddled with malware or other nasty things - these websites should be avoided. For website owners, having a dangerous website can obviously be bad for business if you get hacked and have to tell your customers that you've lost their information or that they contracted malware from your website.
How it works
We have a massive database of vulnerabilities that we’ve built up through some really complicated engineering. This extension is simply querying that database to see if a website you’re on has a vulnerability. There are three states of the plugin. First is that Punkspider has scanned the site you are on and it has no vulnerabilities, if you open up the plugin you should see something like this:
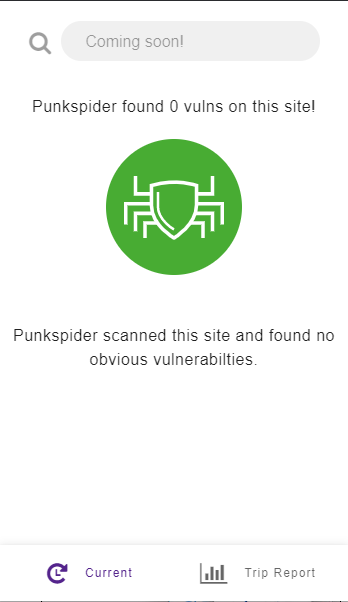
As indicated this means we have checked this site for vulnerabilities and have found it to be clean. Please note: our database contains only the most egregious vulnerabilities and is an automated system. Therefore it can occasionally make mistakes, so be cautious, but know that it at least doesn’t have a horrible vulnerability as told to us by a very carefully engineered vulnerability scanner. The second important state of the plugin is that we have scanned it and found vulnerabilities, in which case you will see something like this:
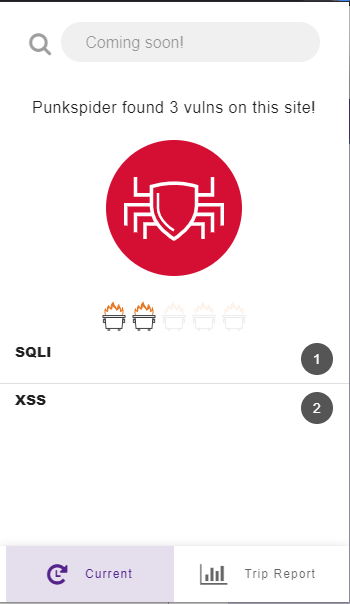
Don’t worry too much about the acronyms on the left (SQLI and XSS in this example), they’re types of vulnerabilities that we won’t go into now. Just know that inputting your information into a site with any of the vulnerabilities we check for is risky. Our dumpster fire-based rating isn’t just a gimmick, these vulnerabilities are very serious, and even a one dumpster fire rating means a website is unsafe. We recommend taking mitigating actions – if you absolutely need to pay for something for example, use Paypal or Amazon Pay, we recommend not to put your credit card or personal information directly into the site. If the site has a login, use a username and password that you have not used on other sites.
The final state of the plugin is that Punkspider has yet to scan the site:
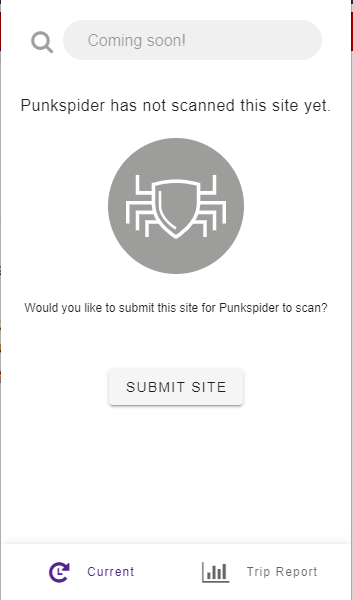
This means we simply haven’t gotten to this site yet. If you would like Punkspider to check this site please click on Submit Site. User submitted sites are given priority, but it still may take some time for results to be returned (possibly even a few days). Please note that this does send QOMPLX the URL that you are visiting – we do not store or keep any of your personal data or identifying data ever, we only keep the site submitted so that we can scan it.
OK, thanks, but seriously what do those acronyms mean?
The acronyms on the left are the various types of vulnerabilities found on the site. If you are new to web security, this probably looks like a bunch of nonsense, but these are abbreviations for the
vulnerabilities that we're checking for. You can read about each one in layman's terms at the links below, but you don't really need to know the details if you're just a casual user, the icon color
and rating are all you need to get started. All of these vulnerabilities indicate an unsafe website that should be avoided. But, if you're curious, feel free to click on some of these links!
SQLI = SQL Injection
XSS = Cross Site Scripting
TRAV = Path Traversal
OSCI = Operating System Command Injection
XPATHI = XPath Injection
I found a vulnerable website, what now?
In the simplest terms, if the website you searched for has any vulnerabilities, you should avoid that website. If you absolutely can't avoid it all together (e.g. you really need that garden gnome statue), try to avoid giving the website any of your personal or financial information. If you need to pay for something on the website, avoid entering any information directly into it – this is where solutions like Paypal or Amazon Pay-like services can come in useful as they do not share any credit or personal info with the website. If you absolutely must create an account on that website, don't re-use any usernames or passwords from any of your other accounts.
I’m a developer and you told me my site is a dumpster fire, you’re wrong and I hate you
Our automated system isn’t 100% perfect. If we’ve made a mistake and need to correct it please email punkspider@qomplx.com and we will correct it immediately.
I have more questions
No problem! Just email us at punkspider@qomplx.com and ask away. We're friendly and responsive, so don't be shy!